Domain enumeration is one of the first thing a threat actor would Attempt to do in order to know where he is and what can be the next steps. I find that CMD commands for domain enumeration are the easiest to detect, will explain why latter, then PowerShell and I believe that the most difficult is when dealing with process injection with WINAPI32. Even if it can be difficult, it doesn’t mean it is impossible to detect and on these blogs I will show the logs and some logic we can use to detect these techniques.
Command Promt
When doing an enumeration via CMD, I realize that most of the common techniques use Windows binaries, this means that for every command we run a new program is executed. With this, you can guess that if we monitor the process created, and the arguments used and we can detect this type of enumeration.
PS: This commands are from: https://book.hacktricks.xyz/windows-hardening/basic-cmd-for-pentesters#domain-info the Pentester Academy course uses PowerShell instead of CMD for enumeration. Which is expected taking into consideration the state of PowerShell detection.
Sysmon and you
Sysmon is really useful tool to get all the necessary information to catch threat actors on early stages. But for this you will need a SIEM where to store, query and alert from the collected logs. Event ID 1 is enough for all the detection on this blog, and also can help detect other attacks, but we can explore those on other opportunities.
If you want to do some test on a simple SIEM you can use docker-elk as it’s easy to deploy and can be really useful to understand some consideration when doing a massive deployment.
Ok lets start…
Let’s detect
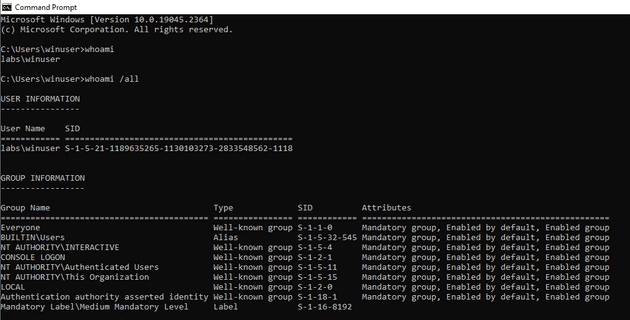
Multiple reports show that after the initial compromise threat actors usually review where they are, what user they have control over and what privileges the user has on the computer. For this on CMD we can use the whoami command. We can get the user we are running and using the /all argument we can see detail information and verify if we have any privileges.
WHOAMI
According to Microsoft: “Displays user, group and privileges information for the user who is currently logged on to the local system. If used without parameters, whoami displays the current domain and user name.”
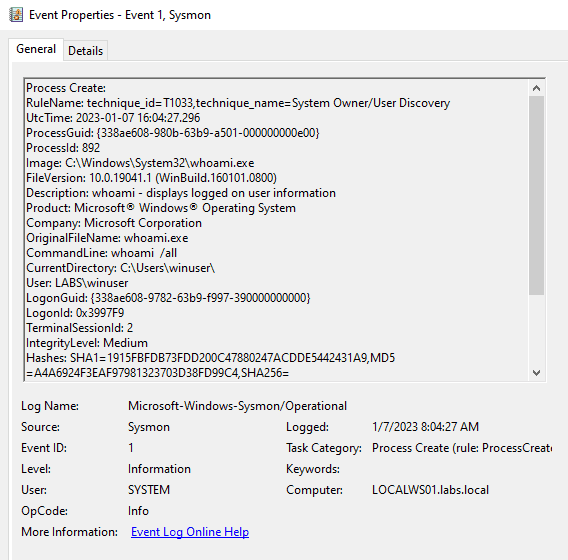
We can see that a new event was generated for this command. We have different parts of the event, the most important for me are:
- ProcessID
- Image
- OriginalFileName
- CommandLine
- CurrentDirectory
- User
- Hashes
- ParentProcess
We can use the different parts of the event to alert on this behavior, let’s start from the worst to want I consider the best. We can alert when a Image string contains “whoami” or when a CommandLine contains “whoami”. Now let’s think how we can evade this, we just need to change the name of the file. It’s that simple to evade a rule that depends on those two fields, let’s try to create a rule more resistant to changes.
We can use OriginalFileName field as this is a little more difficult to change, and most threat actors don’t usually change this. So our rule would be something like:
"OriginalFileName CONTAINS 'whoami'" Let’s be honest, this is not the perfect detection as it can be bypass using a hex editor or a tool to change this field.
Now if we really wanted to detect not only this but all attempt to review what type of functions are used, what registry are query and what objects are access in order to get this information. The main problem with this is the amount of information needed, there are a hundred of process and all of them access many functions, registry, and objects imagine the amount of information this will generate on your SIEM.
Returning to the point of detection, there are cases where whoami is used for applications. In these cases we have to create exceptions, for instance imagine that an application request to know which user is using the app, it may use this command. We will need to review how it normally works and make an exception based on the parent process, the rule will be like:
"OriginalFileName LIKE 'whoami.exe' AND ParentProcess != /(VPN.exe)/".NET
This program is used to configure and manage the OS, for this reason this command can also be used to enumerate local and domain users. This program can be used on production and for good purposes, but there are some arguments that are not used normally. These are the ones we can catch:
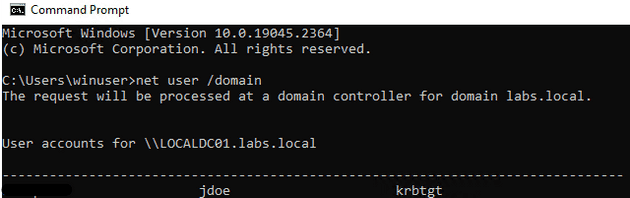
net user /domain
net accounts /domain
net localgroup administrators /domain
net group "Domain Admins" /domain
net localgroup administrators
net localgroup "Remote Desktop Users"
net view /domainWe have to understand something before we can create good rules. First, the “/domain” flag tells net to do a domain search, this is rarely used for benign purposes. We can use this flag to detect some malicious attempts to enumerate users or computer for the domain. Let’s review on of the logs that gets generated when using the command:
We can see that we have enumerated all the users on the domain, with this is an attacker have learned some interesting users to target. Let’s detect this, the events generated for this command are:
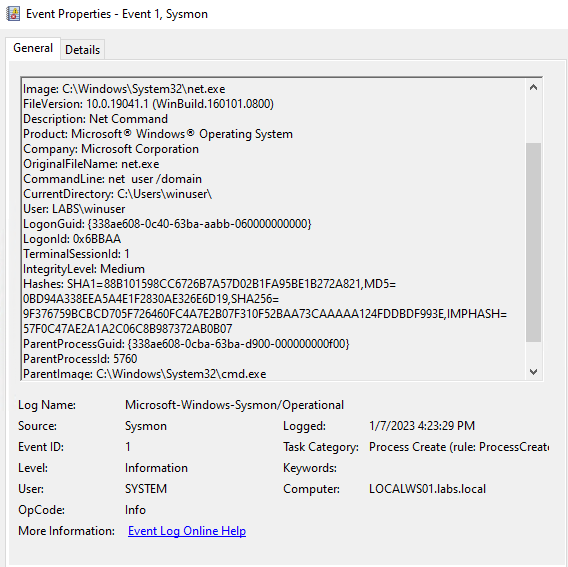
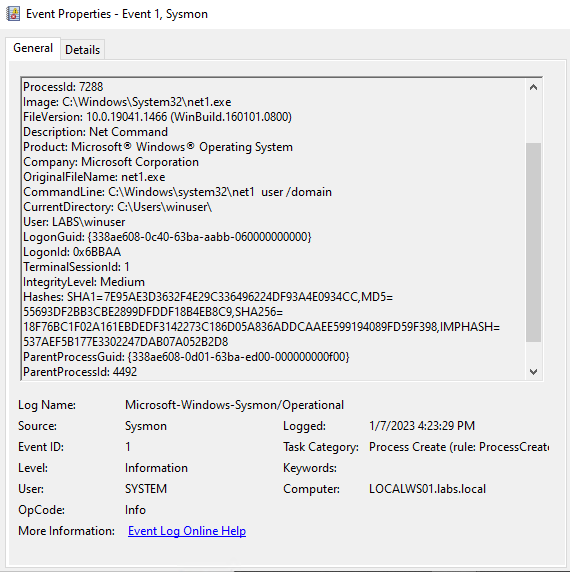
This command generated the expected event but also called a net1.exe to perform the action. In case we didn’t review the event, we could have just look for net.exe and not for net1.exe which could leave a gap on our detection. With this, we can use this information and do a similar rule than the one before.
"(OriginalFileName LIKE 'net.exe' OR OriginalFileName LIKE 'net1.exe') AND CommandLine CONTAINS-ANY [/domain, Remote Desktop Users, ...]".On the link of basic cmd for pentesters, you can find more commands and arguments that may be useful to detect, just remember to review your event and verify that there will be low false positives.
WMI
Describe by Microsoft as “Windows Management Instrumentation (WMI) is the Microsoft implementation of Web-Based Enterprise Management (WBEM), which is an industry initiative to develop a standard technology for accessing management information in an enterprise environment.” is a really powerful component to manage environments. There are some commands that can be used on this feature to enumerate the environment and this can also be detected with what we have been doing until now.
wmic useraccount list /format:list
wmic /NAMESPACE:\\root\directory\ldap PATH ds_group GET ds_samaccountname
wmic /NAMESPACE:\\root\directory\ldap PATH ds_computer GET ds_samaccountnameWe can look for the OriginalFileName and some of the arguments like \\root\directory\ldap and useraccount list
Conclusion
As you may have seen, most of these tools come with Windows by default and that is one of the reason attacker use those. We can detect this type of enumeration with enough visibility but also there are new technique that more advance attackers use. Those are PowerShell and process injection that can make things more complicated, will try to look into those in the future.