Hey, so basically want I want this to be is a simple step to step tutorial to “audit” your gateway, so you can know if you have a vulnerability similar to the one on the podcast.
Secure by defaults
Secure by defaults is the configuration where the device or software comes with the basic functionality to start and you configure it with the features you need. For instance, have you ever use macros on Excel or word? That feature is by default, and now it’s getting block, but is still a dangerous feature on the wrong hands. Like Office, some devices come with different services enable, this services get to enable as soon as you configure in order to provide a fast deployment, but many times users never use those features. In this short experiment I want to explore the configuration of my firewall on the network level.
Identifying the target
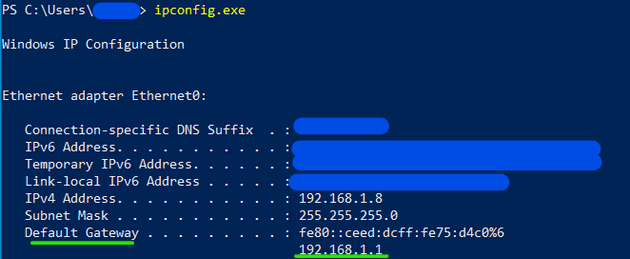
To identify your default gateway we can use different commands, like ´´ipconfig´´ on Windows or ´´ip a´´ o ´´ífconfig´´ on Linux. I’m doing my test on a Windows host, so the output looks like this:
On the image we can see that my gateway is 192.168.1.1, with this information we can start the scanning.
Target acquire
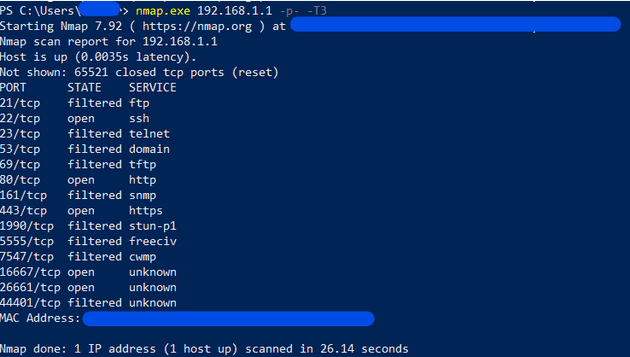
First, let’s explore the ports open on the router. There are different ways to do this, but the most simple one is with nmap. I use this command ´´nmap.exe [Gateway IP] -p- -T3´´, the -p- argument tells nmap to scan all ports and the ´´-T3´´ specifies how aggressive is the scan, I did this to make a fast scan.
We can see that there are a lot of different open ports, we can explore this ports on more details. For instance, port 80 and 443 are the web management interfaces. I think it would be better to use just port 443/https as it provides encryption and most modern computers should be able to support it.
On the other hand, port 1900 gives a 404, and it works with http1.1, not really sure why is this on my router. I could have tried brute force it and find any resource on that port, but I stopped maybe on a next opportunity. Also port 8080 is open and this is protected by a basic form that can be brute force. This port caught my attention as I really didn’t expect this port and the functionality of this is a mystery to me, but I think I can see what’s behind it on the future.
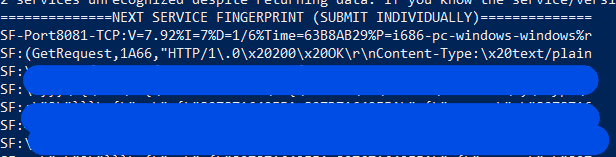
The next two ports 8081 and 8888 gave me a fingerprint that help me identify what maybe the functionality of these ports. The first 8081, is a http1.0 server that gives by default a list of nodes and configurations. Looks like data for a graph, so it possibly that path of nodes that my ISP uses before going to the internet. A really weird case taking into consideration that I as a user really don’t need to see that information so that service could have been attached to the other IPs of the server and not the one that is exposed to me.
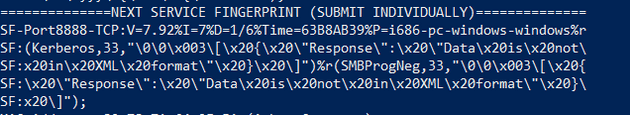
Finally, the port 8888 is the most dangerous in my opinion. On the fingerprint it gives the Kerberos and SMB strings, these are protocols that are used on Windows. Kerberos in particular is used on Active Directory and can be abused to gain privileges on a domain. If my guess is correct, this could mean that a threat actor could break into the domain behind my router and used the foothold to cause problems.
Well, this was an experience. I enjoyed reviewing all of this and learning a little more of some of the devices I use daily and discover some concerning facts about this.
More information: